|
Security Audit nForce Solutions will audit your program in its complete/compiled form (executable/binary) or with its source code. nForce Solutions checks your program to make sure common programming mistakes such as buffer overflow, format string, race conditions, invalid input type, etc. are spotted, adequate security protections are in place and integrated into the program itself to protect the program from malicious exploitation. For more information, contact us! Our security audit service emphasizes strongly on two main areas: system devices and software.
System Devices
nForce Solutions offers two methods of software security audit to help you find and eliminate security holes in your software and assure your business continuity: blackbox and whitebox (source code). Blackbox method involves reverse-engineering the software whereas whitebox or source code audit requires our consultants to manual review software source code to uncover vulnerabilities. The following lists some of the common vulnerabilities that our consultants generally look for:
nForce Solutions offers two methods of software security audit to help you find and eliminate security holes in your software and assure your business continuity: blackbox and whitebox (source code). Blackbox method involves reverse-engineering the software whereas whitebox or source code audit requires our consultants to manual review software source code to uncover vulnerabilities. The following lists some of the common vulnerabilities that our consultants generally look for:
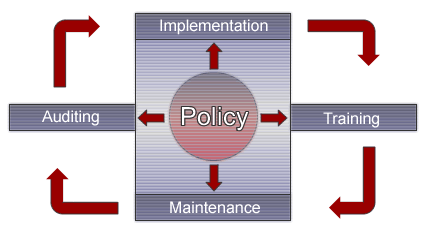
Our PITMA Model The PITMA security framework comprises of the following phases: Policy, Implementation, Training, Maintenance, Auditing. Whether your company is just starting up or has been established and functioning for a long time, PITMA is designed to fit both scenarios. The PITMA security framework gives you a complete security solution so that you don't have to worry about "inadequate security" in any part of your network.
Policy First stage of the PITMA security framework is Policy. Having a Security Policy is the foundation for a solid and complete security solution. In this stage, nForce Solutions will either:
Implementation In order for this stage to be successful, a Security Policy must be existing and current. nForce Solutions will refer to the Security Policy that has been drawn up from the previous stage to implement the security safeguards as directed and agreed upon. This stage includes but not necessarily limited to these steps:
Training Why is Training in the PITMA security framework? Because nForce Solutions want you to be able to maintain the security posture after the Implementation stage. There's no reason to secure your network infrastructure if you don't know how to maintain it. nForce Solutions understand different people have different needs and different types of training are available to suit your needs. nForce Solutions will:
Maintenance nForce Solutions will maintain the security of your network for a period of time (To-Be-Determined upon agreement/contract). The maintenance stage is to verify and assure that your network is operating in a predictable and secure manner. At this very stage, nForce Solutions will:
Auditing Auditing is the final part of the PITMA security cycle, yet it also plays a very important role. Auditing is to verify the correctness of the implemented security controls by performing various security audit against your network to identify weaknesses. nForce Solutions will continuously perform security audit against your network for a period of time (To-Be-Determined upon agreement/contract). At this stage, nForce Solutions will make sure:
This is your one stop complete security solution. You will enjoy the full security services given by PITMA. You will get everything done from A to Z (Risk Assessment, Security Policy Writing, Penetration Testing, Security Training, Security Implementation, etc.). If you're now convinced that PITMA is right for you then please do not hesistate to contact us for quote.
|
Although Outsourcing Development work offers significant savings, companies still need reliable onshore partners to realize those savings. As a Singapore based company nForce Solutions Pte. Ltd. is created to fulfill those needs and become the essential link to a successful partnership between Singapore and Vietnam, and other countries in the Asia region as well. At nForce Solutions, we help you minimize your security risk exposure. nForce's Managed Security Services (MSS) apply our people, processes, technology, and intelligence to help enterprises prevent, detect, and respond to vulnerabilities and threats in real time. nForce's Managed Security Services are designed by certified professionals to allow organizations to cost-effectively outsource their security management, monitoring, and response needs. Comprising five distinctive phases Reconnaissance, Analysis, Penetration, Information, and Documentation, RAPID is a detailed and proven penetration testing approach designed by nForce Solutions Pte Ltd to offer the most systematic and effective way to evaluate the security of a network.
The PITMA security framework comprises of the following phases: Policy, Implementation, Training, Maintenance, Auditing. Whether your company is just starting up or has been established and functioning for a long time, PITMA is designed to fit both scenarios. The PITMA security framework gives you a complete security solution so that you don't have to worry about "inadequate security" in any part of your network. |
© 2006-2009 nForce Solutions Pte. Ltd. |