|
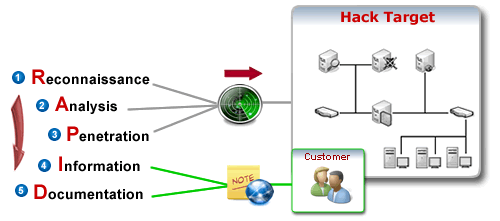
Penetration Testing using the RAPID model nForce Solutions' penetration testing is to tell you whether the "bad" guys can get in or not, there's no "may be" or "uncertainty". The result of this penetration testing is a Yes or a No. You might have seen some other security firms offer their penetration testing service sound similar to something like: "We guarantee that we will be able to find at least one vulnerability from our penetration testing, otherwise you will get your money back, and that penetration testing will be free of charge." While the offer does seem really nice, but it doesn't tell you anything. It doesn't give you any indication that your security architecture or design will be broken. Therefore, nForce Solutions try not to follow that idea of penetration testing and have developed a methodology to do penetration testing more effectively. nForce Solutions.' RAPID penetration testing methodology is designed to ensure the process of penetration happens smoothly, orderly, and of course RAPIDLY. Comprising five distinctive phases Reconnaissance, Analysis, Penetration, Information, and Documentation, RAPID is a detailed and proven penetration testing approach designed by nForce Solutions Pte Ltd to offer the most systematic and effective way to evaluate the security of a network.
[1] Reconnaissance In this phase, nForce will use both passive and active reconnaissnace techniques to identify the customer's network topology, active hosts, IP addresses, OS platforms, open ports, security devices, and many other useful information. All this information will be carefully scrutinized and prepared for the next phase.
[2] Analysis This second phase is where nForce will start to execute application mapping, vulnerability scanning/fuzzing, and vulnerability analysis based on the information gathered previously. Our consultants will attempt to reveal the exact network applications running behind those open ports, identify the associated vulnerabilities, and analyze if the vulnerabilities are exploitable and whether exploitation may cause disruption to the network. If the customer network is found to run dynamic web applications, nForce will perform various vulnerability fuzzing techniques to help discover unknown vulnerabilities due to poor security practices. Some of the vulnerabilities can be discovered during this phase include SQL Injection, Code Injection, Code Execution, Directory Traversal, Cross Site Scripting, et al.
[3] Penetration nForce will exploit vulnerabilities discovered in the previous phase to gain access to the network. There are typically two main vulnerability categories that our consultants will attempt to exploit: network service vulnerabilities and web application vulnerabilities.
[4] Information Upon successful exploitation and having gained access to the network, nForce will immediately notify the customer of the condition and restore the network or system to its original state before the Penetration phase. A quick report of immediate actions (if possible) will be drafted. [5] Documentation The final phase of RAPID Penetration Testing entails our consultants to prepare a comprehensive document explaining the details of how the penetration was possible, what activities were carried out, corrective measures, and possible preventive measures. Risk Assessment There's no way that nForce Solutions can identify, analyze and remove all risks, but instead, risks that cause the most serious impact to your business will be accurately identified and mitigated to an acceptable level. Our risk assessment comprises of the following:
Security Implementation nForce Solutions implement various security countermeasures and safeguards to protect your network from security breaches and hack attacks. Our security implementation service includes but not necessarily limited to the following:
|
Although Outsourcing Development work offers significant savings, companies still need reliable onshore partners to realize those savings. As a Singapore based company nForce Solutions Pte. Ltd. is created to fulfill those needs and become the essential link to a successful partnership between Singapore and Vietnam, and other countries in the Asia region as well. At nForce Solutions, we help you minimize your security risk exposure. nForce's Managed Security Services (MSS) apply our people, processes, technology, and intelligence to help enterprises prevent, detect, and respond to vulnerabilities and threats in real time. nForce's Managed Security Services are designed by certified professionals to allow organizations to cost-effectively outsource their security management, monitoring, and response needs. Comprising five distinctive phases Reconnaissance, Analysis, Penetration, Information, and Documentation, RAPID is a detailed and proven penetration testing approach designed by nForce Solutions Pte Ltd to offer the most systematic and effective way to evaluate the security of a network.
The PITMA security framework comprises of the following phases: Policy, Implementation, Training, Maintenance, Auditing. Whether your company is just starting up or has been established and functioning for a long time, PITMA is designed to fit both scenarios. The PITMA security framework gives you a complete security solution so that you don't have to worry about "inadequate security" in any part of your network. |
© 2006-2009 nForce Solutions Pte. Ltd. |